DarkFlash
Instantly Detect & Retrieve Data Breaches with our Dark/Deep Web Monitoring Solution
Request A DemoWhy DarkFlash?
DarkFlash reveals early warning signals from underground cybercriminal ecosystems
Key Features
From underground threat discovery to early attack prediction, before damage occurs.

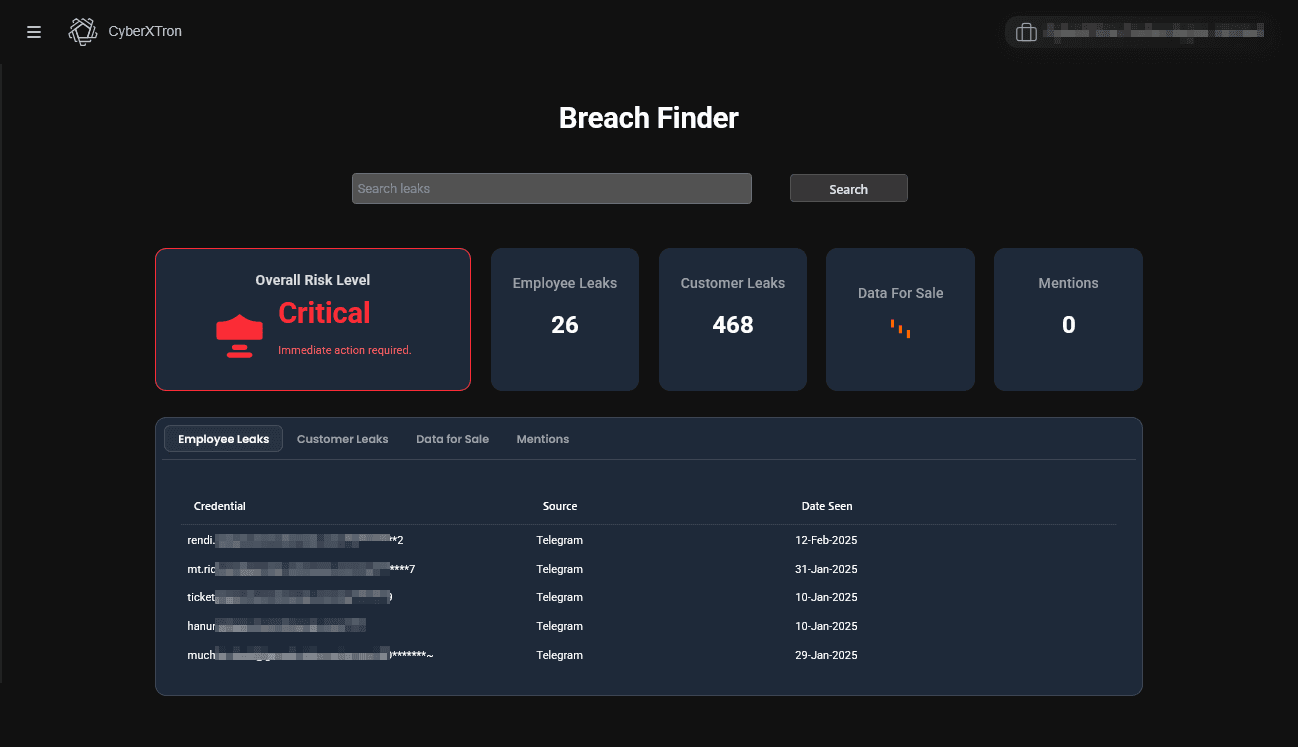
Credential Leak Monitoring & Retrieval
Timely Detection
Rapidly identify compromised credentials.
Prevent Unauthorized Access
Safeguard your accounts and data.
Minimize Cyber Risks
Reduce the risk of security breaches.
Real-time Monitoring
Continuous vigilance for credential threats.

Personal Identifiable Information (PII) Breach Detection
Comprehensive PII Surveillance
Monitoring personal identifiable information (PII) breaches across diverse forums.
Swift Identification
Rapidly spotting PII exposures by threat actors and hacktivists.
Data Privacy Protection
Safeguarding sensitive personal information.
Regulatory Compliance
Ensuring adherence to data protection laws.

Source Code Leak Detection in Code Repositories
Cross-platform Vigilance
Monitoring code leaks on GitHub, GitLab, and Paste Sites.
Timely Detection
Rapidly identifying source code exposures.
Intellectual Property Safeguard
Protecting your valuable code assets.
Competitive Advantage
Securing your unique code from prying eyes.

Identification of Private & Sensitive Document Leaks
Holistic Document Oversight
Comprehensive surveillance of business-related document leaks.
Real-time Alerting
Immediate notifications of potential leaks.
Risk Mitigation
Protecting sensitive data from unauthorized exposure.
Regulatory Compliance
Ensuring adherence to data privacy regulations.

Guarding Your Financial Security
Comprehensive Coverage
Extensive monitoring of dark web card shops and channels.
Swift Detection
Rapid identification of cloned credit card details.
Proactive Defense
Protecting against fraudulent transactions.
Data Security Assurance
Ensuring your financial information is safe.
Value to Your Team
Insights, automation, and intelligence tailored to your team’s security mission.
CISO
Gain early visibility into leaked credentials and underground attack planning, enabling proactive, risk-informed decisions before threats reach your environment.
Explore More

SOC Manager
Threat Hunter
Maintain continuous dark and deep web oversight with documented evidence of credential exposure management and automated reporting aligned to regulatory frameworks.
Explore More

Compliance
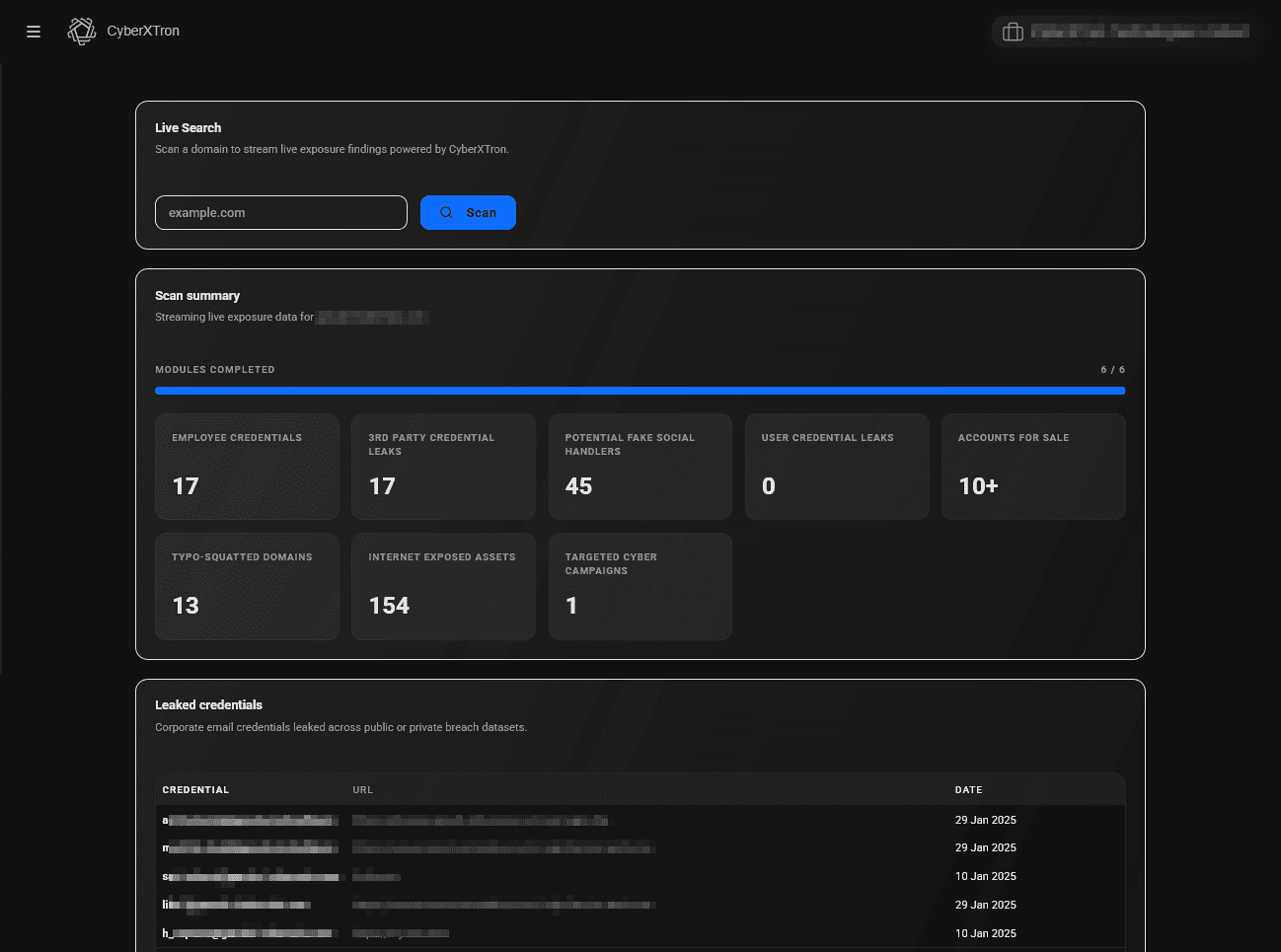
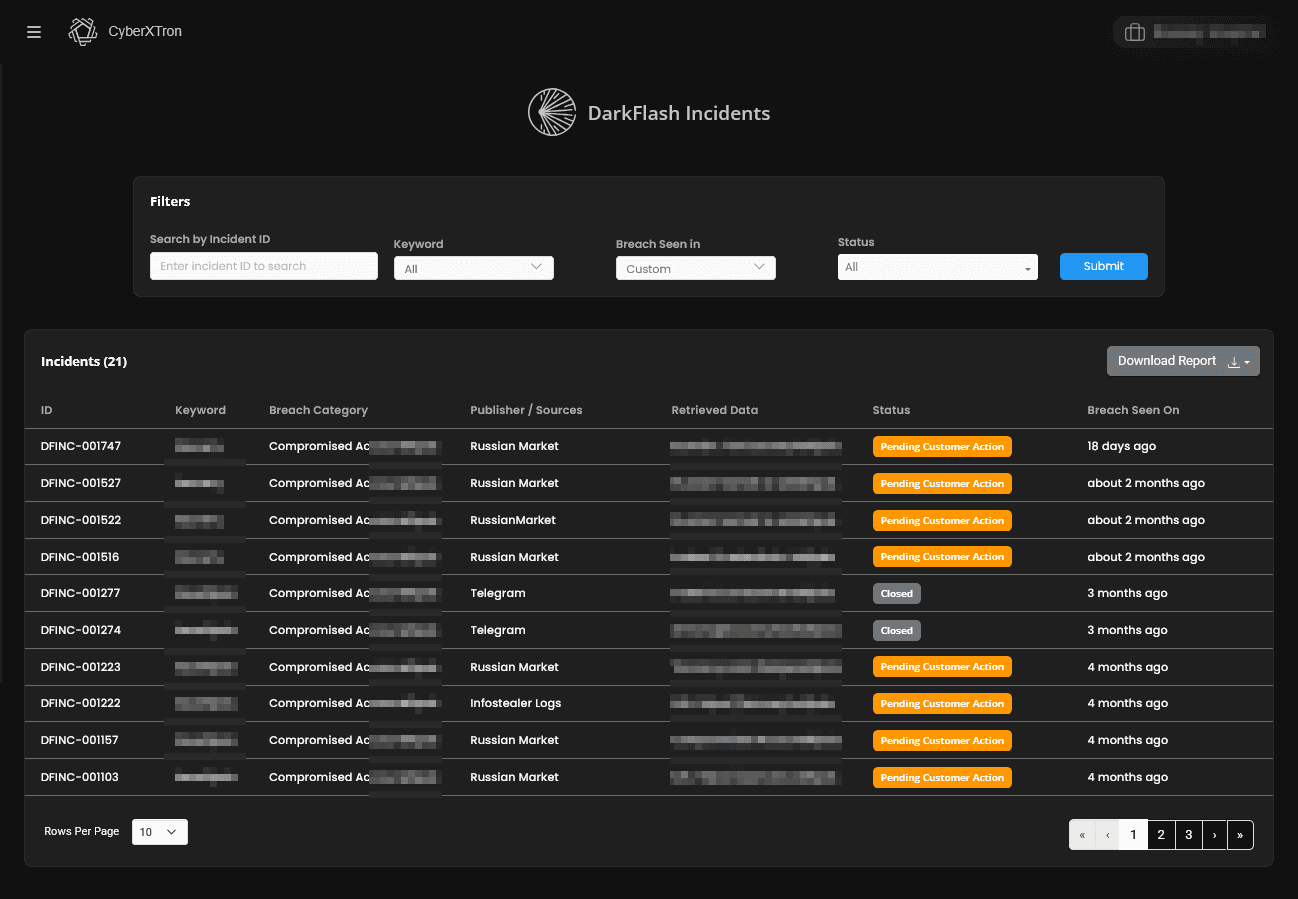
See DarkFlash in Action
Get a real-time view of how DarkFlash detects leaked data, exposed credentials, and hidden threats across the deep and dark web.
FAQs
Get clarity on how DarkFlash uncovers hidden risks and empowers your security team to act faster.