
India Under Cyber Siege: 40+ Hacktivist Groups joined hands and Targeting Key Sectors Post-Operation Sindoor
Executive Summary:
CyberXTron researchers are currently monitoring over 40 hacktivist groups—most notably Keymous+ and AnonSec—that are allegedly coordinating cyberattacks against Indian government entities and critical infrastructure. The campaign is believed to involve website defacement, distributed denial-of-service (DDoS) attacks, and data exfiltration, with reports of successful breaches affecting several Indian government websites. The attackers have also outlined future targets, including the Indian Army, Air Force, Navy, and the Ministry of Defence. This wave of activity reflects a politically motivated cyber offensive aimed at disrupting national operations and eroding public trust. This advisory aims to raise awareness and provide actionable intelligence and technical countermeasures to combat targeted cyber attack campaign.
Origin and Attribution
Pro-Pakistan hacktivist communities and have previously engaged in politically motivated campaigns focused on Indian entities.
Their current claims include future attacks on high-profile defense organizations such as the Indian Army, Air Force, Navy, and the Ministry of Defence. These declarations appear to be part of a coordinated psychological and ideological operation intended to intimidate and provoke.
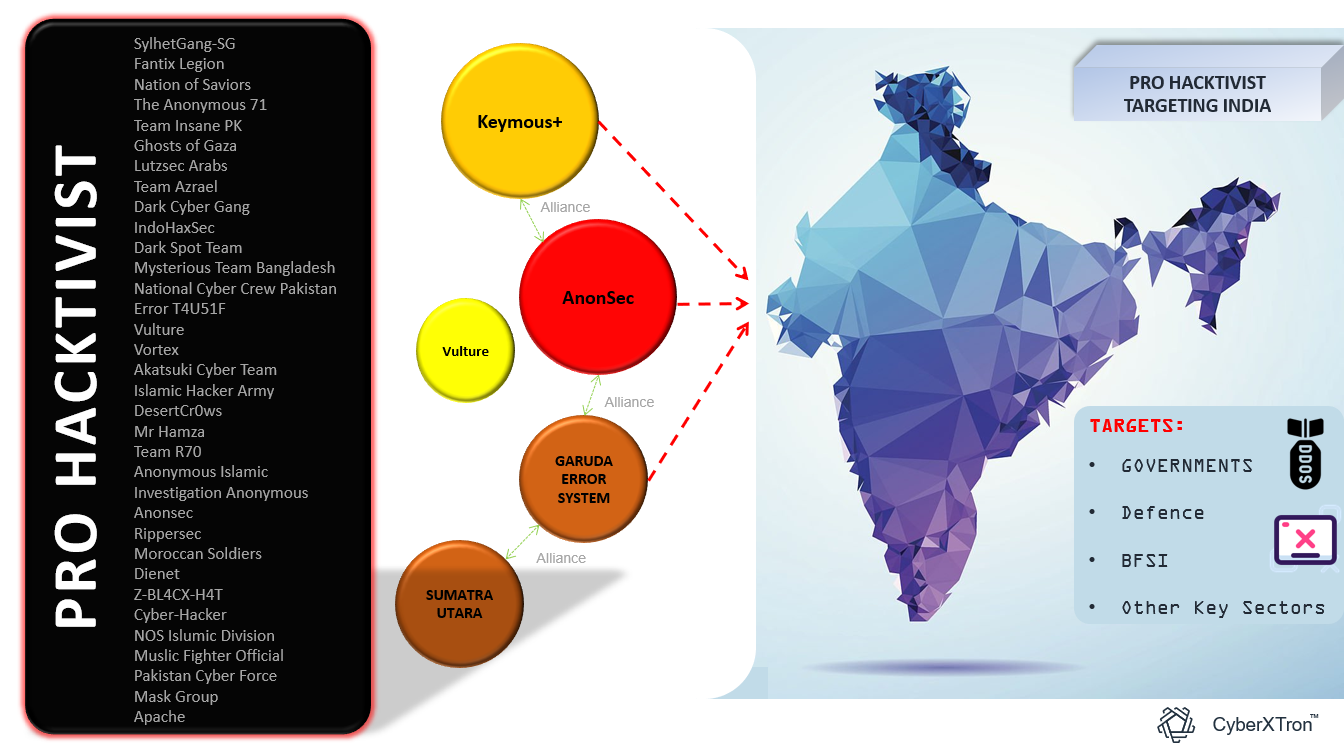
Fig: Multiple Pro-Hacktivist Targeting India Cyber Space
Ongoing Monitoring by CyberXtron Team
The CyberXtron Threat Intelligence Team has been actively monitoring and maintaining detailed profiles of the hacktivist groups Keymous+ and AnonSec, tracking their historical activities and potential threats to Indian digital infrastructure."
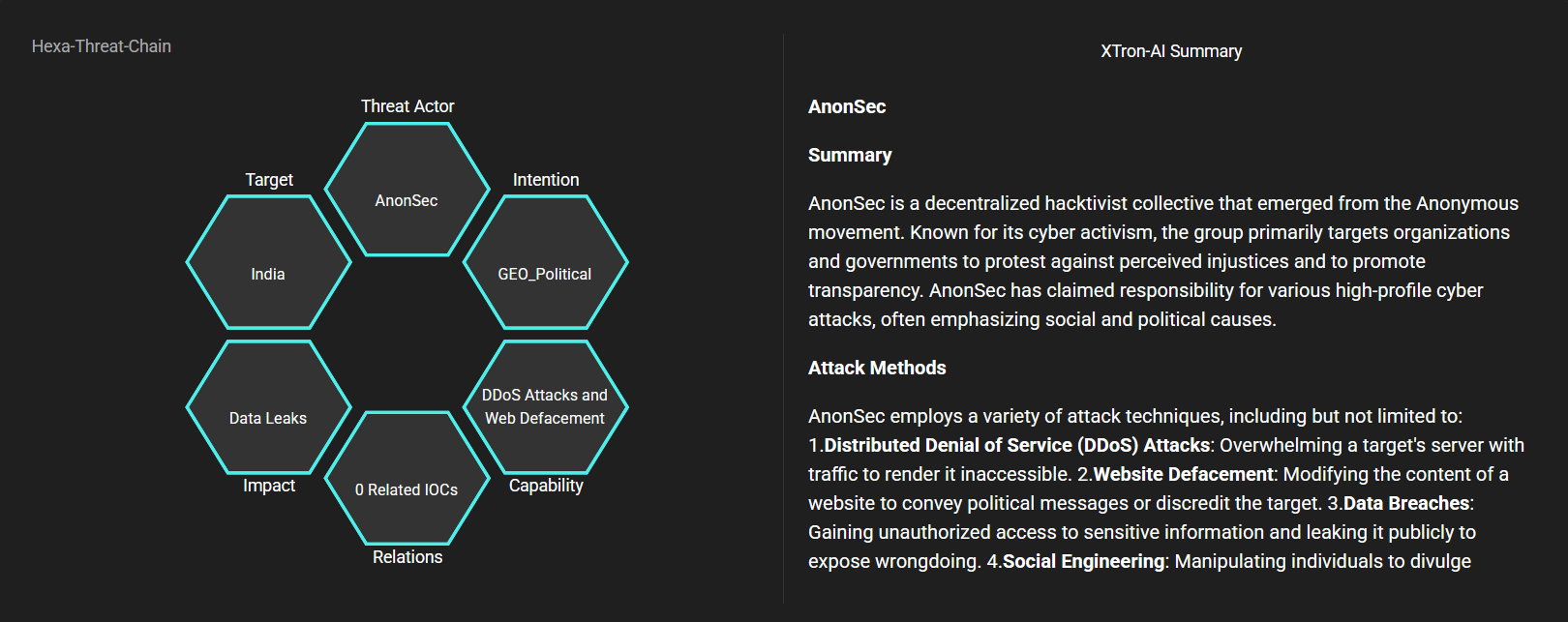
Threat Actor: AnonSec
Threat Actor: Keymous+

Targeted Sectors:
As of now, the following websites are actively being targeted by cyber threat actors:
- Government-related site, often a high-profile target for state-sponsored or hacktivist groups.
- A defense sector website, vulnerable to nation-state actors seeking sensitive military and strategic information.
- A critical infrastructure website, likely tied to key services or industries.
- Another key sector site, related to financial or telecom industries.
These targeted sector represent the most immediate threats, and the list is continuously updated as more entities come under attack in the ongoing cyber threat landscape.
The following is a list of websites that have already been targeted, according to communications from threat actors (it is important to note that most of these websites are currently live and accessible)
- Government e Marketplace (GeM)
- National Judicial Data Grid (NJDG) Official
- National Commission for Women (NCW)
- Election Commission of India (ECI)
- Public Enterprises Selection Board (PESB)
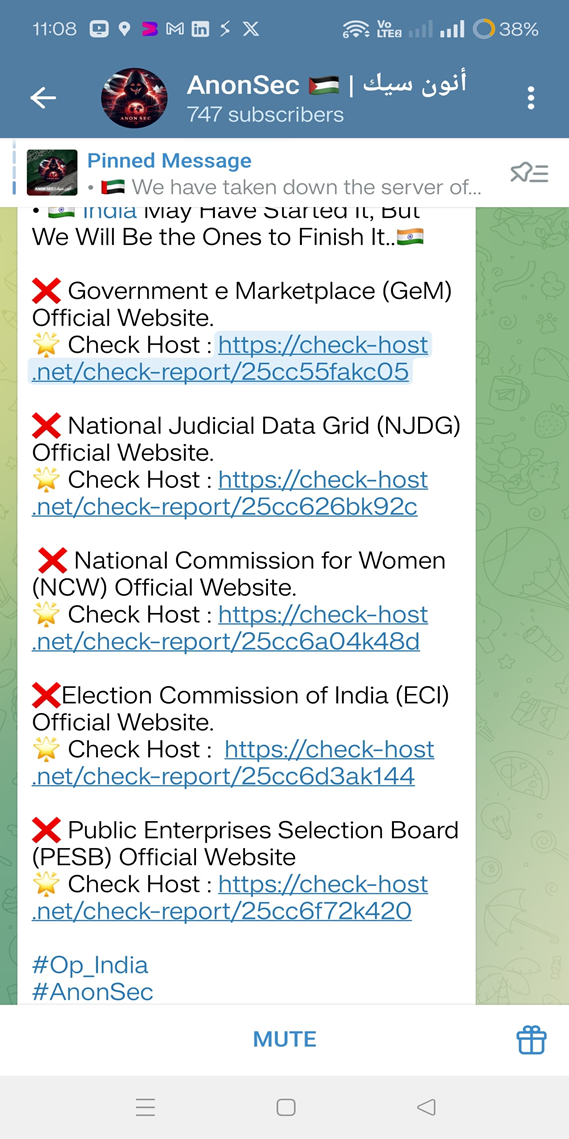
Fig: Anonsec claims to have targeted multiple Indian government websites
Other Claims:
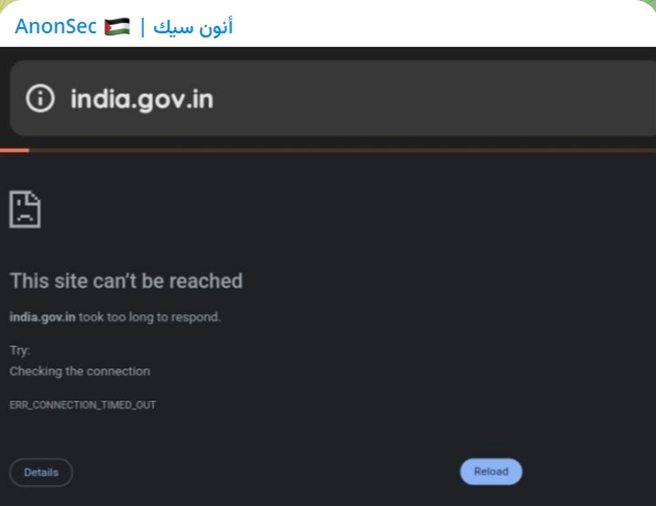
- National Portal of India (india.gov.in)
- National Informatics Centre (NIC),India
- Indian Overseas Bank (IOB)
- Bank of Baroda
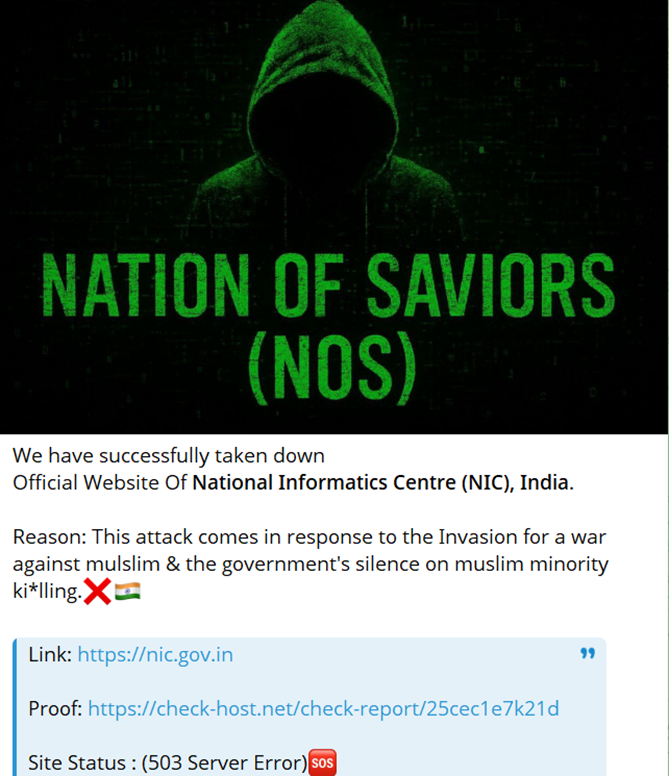
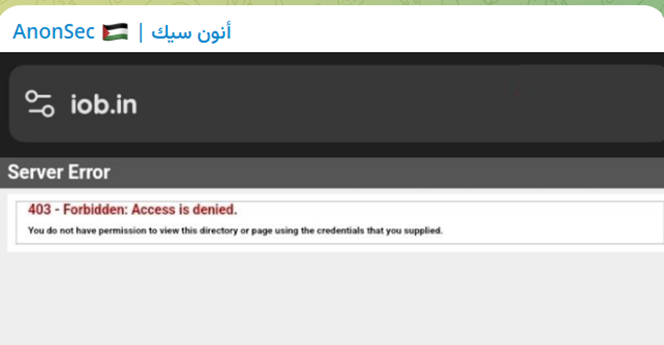
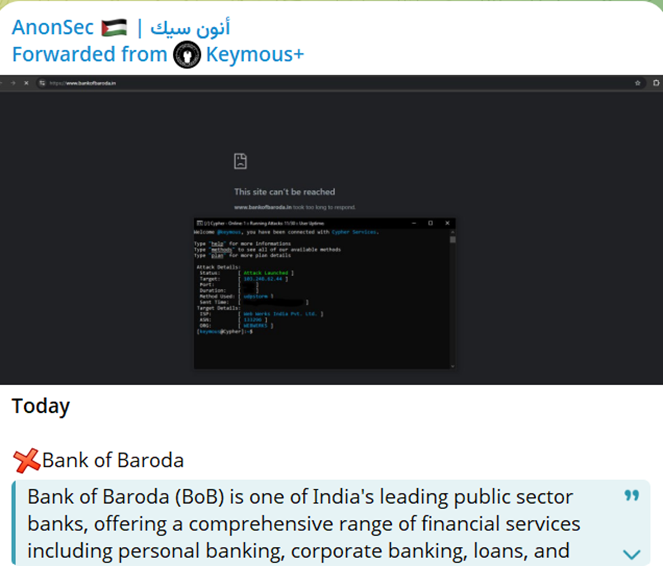
Hacktivist Alliances - Expanding the Reach of Cyberattacks:
Threat actors are forging alliances with other high-profile hacktivist groups to significantly amplify the scale and impact of their cyberattacks. By collaborating with like-minded factions, they are pooling resources, intelligence, and expertise, enabling them to target a broader range of sectors and infrastructure. These alliances are allowing them to launch more sophisticated, coordinated attacks that are harder to detect and mitigate.
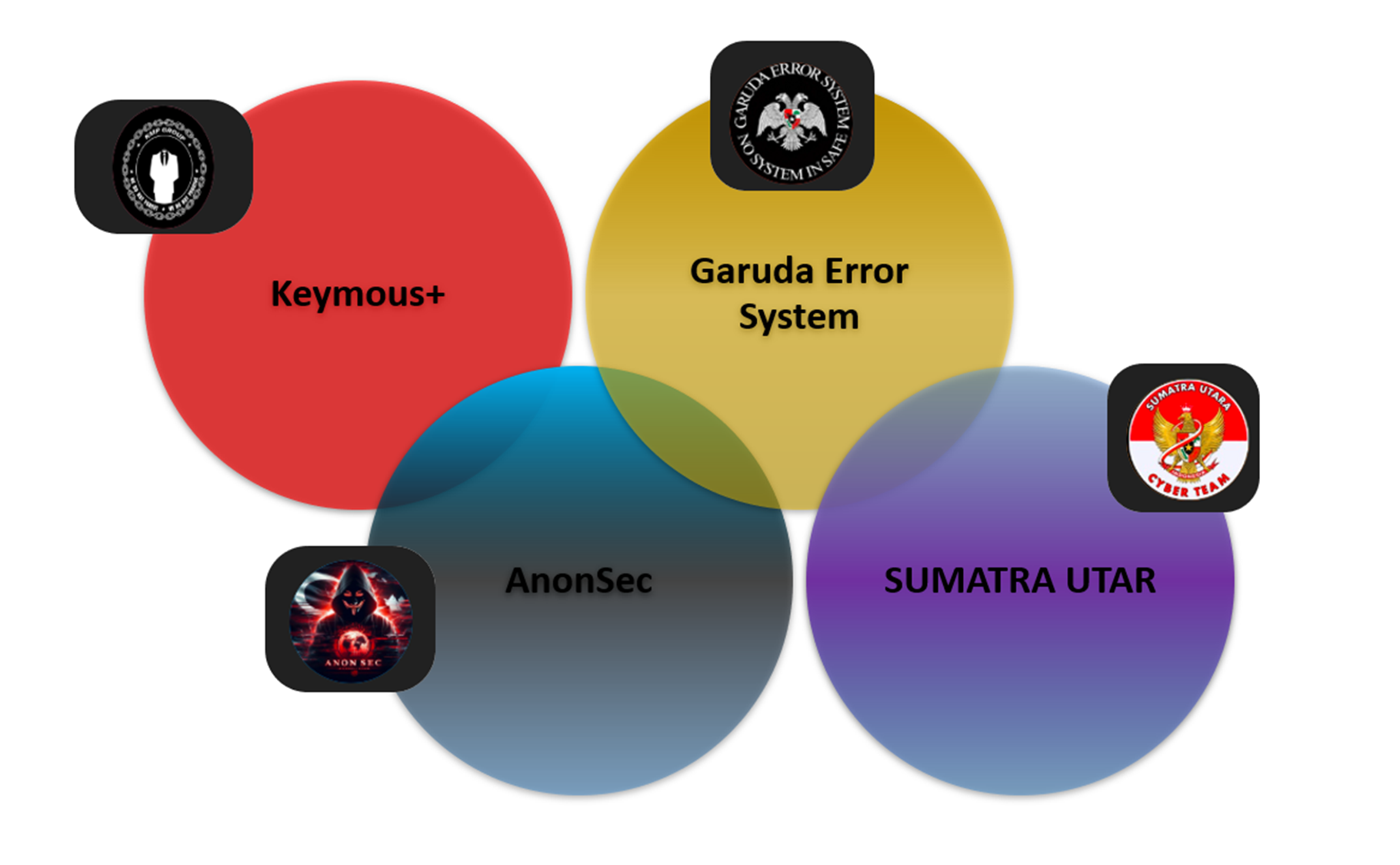
Threat Actors & Their Alliances:

Primary Attack Methods:
- DNS Reflection/Amplification Attacks: Hacktivist groups are leveraging vulnerable DNS servers to amplify rogue DNS requests, generating a high volume of DNS response traffic directed at the victim’s public IP addresses or websites.
- TCP Flood is a Layer 4 (Transport Layer) Denial of Service (DoS/DDoS) attack that exploits the TCP three-way handshake to overwhelm a server with half-open connections, eventually exhausting system resources and making the service unavailable.
- HTTP Flood is a type of Layer 7 (Application Layer) Distributed Denial of Service (DDoS) attack where the hacktivists overwhelms a web server or application with seemingly legitimate HTTP requests, exhausting server resources and making the service unavailable to legitimate users.
- RUDY (R-U-Dead-Yet) is a Layer 7 (Application Layer) DoS attack that targets web servers by slowly sending HTTP POST requests, one byte at a time. Its goal is to exhaust server resources by keeping many connections open for as long as possible.
- Other Reflection & Amplification attacks are powerful Layer 3/4 DDoS techniques that allow attackers to multiply traffic volume while hiding their identity by spoofing the victim's IP address, generally exploiting well-known UDP services (such as NTP, Memcached, Chargen, SSDP, etc).
2. Web Defacement: Hacktivist groups are targeting PHP file upload plugins using the "Alone injector.php"—a vulnerability in PHP applications that allows attackers to inject malicious code and gain unauthorized access and control over the system. This type of code injection attack, specifically PHP code injection, exploits scripts that contain functions enabling the execution of system commands. As a result, attackers modify the victim's website content to display hacktivist messages and images.
Technical Recommendations and DDoS Mitigation countermeasures:
- Implement perimeter controls/firewall rules to filter large or fragmented ICMP packets and UDP reflection/amplification attacks:
Restrict ICMP type echo-request with length 1501:65535.
Restrict UDP traffic on port 123 and block packets larger than 50 bytes. - Restrict UDP traffic from source port 53 and block packets larger than 512 bytes (DNS reflection/amplifcation attacks).
Restrict UDP traffic on port 1900 (SSDP).
Restrict UDP traffic on port 11211 (Memcached).
Restrict UDP traffic on port 19 (Chargen).
Restrict UDP traffic on port 389 (LDAP). If LDAP doesn't require UDP, disable it on your server. - Deploy Web Application Firewall (WAF) controls to mitigate bot-originated traffic.
- Deploy TCP 3-way handshake verification controls to combat TCP-SYN flood attacks.
- Ensure your cloud volumetric DDoS monitoring thresholds are properly configured to detect unusual traffic spikes in the above-mentioned protocols/services.
- Evaluate your DDoS incident response process (perhaps with a tabletop exercise).
- In the case of on-premise/inline DDoS protection solutions, make sure to enable on-demand HTTP authentication controls in case of abnormal HTTP requests.
- Secure your Web Server Configuration by disabling unnecessary features or modules (mod_autoindex, mod_status).
- Ensure directory listing is disabled to prevent attackers from viewing sensitive files.
- Use strong SSL/TLS encryption for secure connections (preferably TLS 1.2 or 1.3).
- If using a CMS (e.g., WordPress, Joomla), ensure it is properly configured and secured.
- Use security plugins/modules designed to detect and block malicious activity (e.g., Wordfence for WordPress).
- Regularly change default admin passwords and usernames.
- Use IP whitelisting to limit access to the admin panel or backend and Implement two-factor authentication (2FA) for all administrative accounts and critical user roles.
Conclusion
In conclusion, while hacktivist cyber attacks present a growing threat, they also offer an opportunity for defenders to strengthen their cybersecurity posture and resilience. By proactively adopting robust defenses, enhancing threat intelligence capabilities, and staying informed on emerging attack trends, organizations can not only mitigate risks but also position themselves as leaders in cybersecurity. Together, we can ensure that the digital landscape remains secure, and that defenders continue to stay one step ahead of those who seek to disrupt it.
At CyberXTron, we specialize in Autonomous Digital Risk Protection and AI-driven Threat Intelligence tailored for protection against hacktivist threats and targeted cyber-attacks.
Click here to Book a free consultation with our expert team!!!